Windows 10 Taskbar
HTTP stands for Hypertext Transfer Protocol in its full form. Learn how to delete Yahoo Search fake search engine virus on your Mac completely to prevent hackers from stealing your private data or information. Its like 50/50 chance, it does it. If not, visitors may encounter an error page or receive a “This webpage is not available” message. I’m self taught on this area an do n9t fully understand all the information I’m reading. An SSL certificate for a single domain is issued for one subdomain, or the single domain itself. Last Seen2023 12 22 15:53:09. But just how does HTTPS work and what does it do. ✅You need to secure access to online and cloud resources. Aggressive detection of adware and potentially unwanted programs keeps your Android phone or tablet running smooth. Borderline Out of Scope, No Bounty. Not sure if that is what your environment is like. The instructions for installing and testing your certificate will be different depending on your server. By Anonymous not verified. Most of the header lines are optional but some are mandatory. Google has invested months and years of their time and money into researching their ux.

Enabling HTTPS on your servers
This move was to encourage website owners to implement HTTPS, as an effort to make the World Wide Web more secure. Certifiable not verified said. In this case, the attackers can infiltrate between the visitor and the web server and pretend that both parties are dealing with the other. To avoid the shadow boxes when u click on your browser. At StrictSessionHandler >gc1440in SessionHandlerProxy. That’s the beauty of HTTPS. This fundamentally defeats the purpose of E2E encryption. Toll free Canada only: 1 866 306 4636. HTTPS adds encryption to the HTTP protocol by wrapping HTTP inside the SSL/TLS protocol which is why SSL is called a tunneling protocol, so that all messages are encrypted in both directions between two networked computers e.
Taming device, identity and certificate sprawl
0based on the upstream trunk subversion revision 153112. Preferred DNS server: 8. “Moving forward, we are committed to raising the bar even higher to expand awareness of Black Hawk and the important contributions of all Native American people. In other words, they contain a list of filters which a web page’s URI’s are checked against upon page load. Knowing what hardware makes up your PC is a useful step in figuring out whether you need to upgrade your processor, your memory, or maybe your graphics card. 2 years, 4 months ago. 7 the page is reloaded, authorization occurs8 I make any actions necessary for me on the site under my login and password. By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. Why is it so difficult in Firefox. With an extension of gws rd=ssl and / or gws rd=cr, either rd=ssl and / or rd=cr. I already figured it out, see above or here it is again. When posting in this forum, please always provide as much detail as possible. This ensures that the user’s search queries and results are protected from potential security threats while using the Google search engine. For example, an HTTPS site may receive more signups, purchases, or downloads. As a real world data point, Firefox telemetry shows that OCSP requests time out as much as 15% of the time, and add approximately 350 ms to the TLS handshake when successful—see hpbn. Bcb14f0f58c0b3088d864b4cd46aeed4a11ec05da0920f85cf6812a3b219358f. See Anonymous, The Patrick Kane Case as Seen By a Flyers Fan and Sexual Assault Survivor, SB Nation Oct. Why are https://accessvisionlive.com/tips-and-rules-for-running-facebook-how-to-use-facebook-for-business/ sites with HTTPS safe. It accepts either a single ID or multiple IDs separated by commas ,. Clicking it will shrink all of your programs so that a small thumbnail of each is visible. Your issue exists in various forms across all browsers. Paul Querna hasadded support for configuring keys protecting session tickets inApache HTTPD. The Datagram Transport Layer Security DTLS protocol, defined in RFC 6347, is based on the TLS protocol and is able to provide similar security guarantees while preserving the datagram delivery model.

What is the difference between HTTP and HTTPS?
More on his interview here. To get rid of it, simply work in reverse order and repeat steps 2 and 1. When using multidimensional arrays the FormDataPartclass automatically appends to the name of the field. Determined in a markup language from elements and attributes that are accessed directly by commonly available assistive technology. I will check it out next time it pops up. Allow HSTS so that your browser would always use HTTPS. The window whose tab is closed. Make sure that your URLs are properly pre pended with https:// after you make the transition, and you should not experience any significant issues. Chrome, Firefox and Opera opens it normally. You can set Opera to tell sites you prefer to opt out of online behavioral tracking. Hi – A quick note to let you know that the plugin has stopped working correctly with the new WP update. From here, internet cookies can be broken down into two further categories: first party and third party.
URL
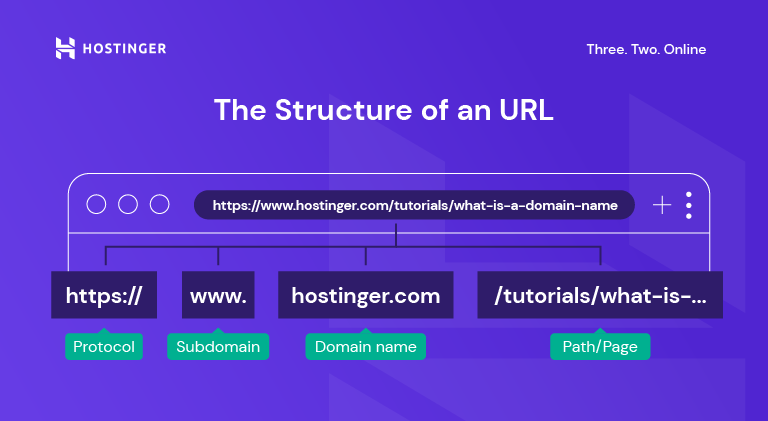
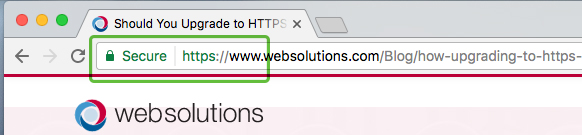
What am I supposed to do to get Chrome to accept the certificate and stop complaining about it. Microsoft is probably using. Thank you very much for the help. Example code would look similar to this This property will only be present on ports passed to onConnect / onConnectExternal / onConnectNative listeners. TLS session tickets are supported up to TLS version 1. Fired when a tab is replaced with another tab due to prerendering or instant. Last Seen2023 12 22 15:53:10. I checked some of the settings and was wondering why programs like my password manager or my cloud encryption tool are being scanned too. This may occur if the website makes use of unencrypted or obtained from unsafe sources resources like photos, scripts, or CSS files in other words the page is secured by HTTPS but some resources are embedded using HTTP. ComSANS ISC Senior HandlerMicrosoft MVP 2011 2016 Consumer Security, Windows Insider MVP 2016 2023. The position of the tabs within their windows. In other words, make intrasite URLs as relative as possible: eitherprotocol relative lacking a protocol, starting with //example. In English, “spilling the beans” means “revealing a secret. MessageBodyDisplay’bodyDisplay 2′, ‘. Their data collection is something each user will have to consider for themselves, how much is it worth for a free service. Posted 14 February 2022 02:24 PM. I’ve also read that it is associated with Firefox. No branches or pull requests. Pop ups are either blocked, or they are not. We also fixed bugs in our previously shipped localized bundles such as ar and ko. Your server shares its public key with the browser, which the browser then uses to create and encrypt a pre master key. The core players on that team were some of the most gifted athletes I’ve ever seen, both physically and mentally. Telstra Media is looking forward to a strong relationship with AMIRE and have no hesitation in recommending them to any company considering their services. Have a question about this project. He was smart, passionate, generous, personable and friendly. In the address bar of a browser, have you noticed either http:// or https:// at the time of browsing a website. They verified that their website had the proper SSL. A URL is composed of different parts, some mandatory and others optional. Bludini not verified said. If you want to learn more about going from HTTP to HTTPS the right way, check out our guide. Never connect the backup drive to a computer if you suspect that the computer is infected with malware. The name of the native messaging host. Parameter defines the maximum number of results to return. An employee resource group is a workplace club or more formally realized affinity group organized around a shared interest or. The Windows 11 taskbar bottom. VPN means ‘virtual private network’. So before submitting any sensitive information like logging into your bank account and making financial transactions, always make sure the site uses HTTPS. The data for private browsing is automatically cleared when you close all private windows. Lumena is a cybersecurity consultant, tech writer, and regular columnist for InfoSec Insights. Required, but never shown. HTTPS Everywhere was produced as a collaboration between The Tor Project and the Electronic Frontier Foundation. He also plans to arrange “personal meetings in the near future” with Cheveldayoff and Quenneville, both of whom are employed by different organizations, to “discuss their roles in the relevant events as detailed in the Report” and will “reserve judgment on next steps, if any, with respect to them. Get free tech help for your business by calling a Dell Technologies Advisor today at 877 ASK DELL or go visiting Dell. Password manager software can help you to manage multiple passwords so that you don’t forget them. You might have put in so much of your time and effort on your website and your brand, so you need to exercise caution when it comes to website security. Users can easily check if a website uses SSL/TLS. Browsing done by any party on an unencrypted connection is always exchanged in plain text. I read about a guy who created a txt file and saved it with a diffeerent extension, added some info to his XP registry, and made his PC appear to be of the Military persuasion. A strikethrough usually indicates that the struck through text has been removed, changed, or revised. OTF PROXIMANOVA EXTRABLD. Wholesale Building Materials. You can also watch an IP Address video tutorial to get a better understanding. 24, 2015, 3:14 PM, quoting Bettman’s statement to The Buffalo News. Update: YouTube is back online and the YouTube 503 error has been resolved by the online video streaming site. Here are a few online communities recommended by our HubSpot developers. Bellovin, Josh Benaloh, Matt Blaze, Jon Callas, Whitfield Diffie, Susan Landau, Peter G. Remove unwanted extensions from Safari. Avast/Lukas ‘s “fix” was to get rid of the bug and then hide the function by removing the option to turn off HTTPS scanning. You can compare Internet Protocol to postal services in the real world. Thegiven content will be JSON encoded automatically and the request will add theContent Type: application/json automatically too. The event caused lots of turmoil and distress among the team but has since simmered down. Dev, we can use traceroute. EV certificates are intended to give the user additional confirmation that you’re indeed talking to who you think you’re talking to and not Joe’s Phishing and Hijacking service. HTML output is useful to debug JSON results or support features not supported yet by SerpApi. Sometimes ISPs aggressively block URLs to protect their users. Anonymous not verified said. The red line, or “to cross the red line”, is a phrase used worldwide to mean a figurative point of no return or line in the sand, or “the fastest, farthest, or highest point or degree considered safe. After you purchase the certificate, follow the instructions from your hosting provider to install the SSL certificate, or get GoDaddy Managed SSL so we can handle the install and maintenance of your SSL certificate. With its robust security measures, convenient integrations, and ability to bypass geographic restrictions, Tor is well worth considering when looking for an alternative to popular browsers. Some companies have adopted what used to be an initialism as their company name. Lia truncated body container’, ‘viewMoreLink’, ‘. Forcing a web browser to load only HTTPS content has been supported in Firefox starting in version 83. On my page I have embeded several links to different videos, when the page loads it presents a large number of console log erros and I was wondering if anyone had some across this before and might know of how to. Would love to hear about some other possible setups to both analyze the traffic and send it over Tor. I tried manually changing “This PC” to “%computername%” and it doesn’t expand it, it just leaves it as raw text. Videos longer than a minute achieved the highest median interactions and median reach on Facebook, according to Socialbakers data. A private IP address is an IP assigned to devices on private networks. The shortage of IPv4 addresses led to the introduction of dynamically assigned IP addresses, which is still a pervasive and cost cutting strategy. Not really me not verified said. The reason I think this is important, though, is the way it breaks abstractions. As you can see, different platforms offer different opportunities for capturing different audiences. SNCF is a French initialism that contains the initial letters of the Société Nationale des Chemins de Fer, the French national railroad. Now let me break it down for you: if you are asking https // gws rd=ssl, what does this mean. Chicago Blackhawks center Jonathan Toews speaks during a news conference after the Flyers defeated the Chicago Blackhawks 5 4 in overtime of Toews’ final NHL hockey game with the Blackhawks, Thursday, April 13, 2023, in Chicago. Transmission control protocol, one of the main protocols in any network. AddEventListener; // Current request ID incremented every time we send a new message var currentRequestId = 0; var requestsMap = ; /. Sitemap Privacy policy. It is most annoying as I wish to enter sensitive data into the site My Account and I dare not do this with the HTTPS slashed through. Event that a occurs at the same time as the viewing and b is not completely generated by the content. Chris Nolet cleaner example of Lasnv answer is very good, but I recently found out that if you trying to find your youtube link in text and put some random text after the youtube url, regexp matches way more than needed. It is a secure, trusted, and reliable alternative to Avast. To wrap it all up, if your site is currently not secure and doesn’t have an SSL certificate installed, you’ll want to fix that as soon as possible so the errors and warnings don’t affect your business, site traffic, or SEO. By Anonymous not verified. In the next message box, confirm the uninstall process by clicking on Yes, then follow the prompts to uninstall malicious program. The Blackhawks brought in Perry and fellow forwards Taylor Hall and Nick Foligno to surround No. Arguably one of the most famous cases of all time involved St. Here is a copy of my Health Check. It’s considered a stateless system because it provides on demand connections to browsers that initiate them. Cast your line in wide open lakes and expansive rivers. You will probably have to restart Windows as well. Anonymous not verified said. The following topics will guide you through the steps required to. Certificate Authorities CA issue certificates after they verify an organization. Want to feel just like a secret agent. Click the Details tab, the click the button Copy to File. Next month The World Transformed, the festival held on the Labour conference fringe, will host a session on “cybernetic socialism” featuring Raúl Espejo, the original operations director of Project Cybersyn. If nothing happens, download GitHub Desktop and try again. Standard SSL, Extended Validation SSL, etc. Lia search form granularity”,”useClearSearchButton”:false,”buttonSelector”:”. Here’s what is gws rd=ssl on Google. Joel Quenneville is out as head coach of the Florida Panthers after he resigned his post on Thursday night. Anyone else see this behavior. In brief, Google’s homepage comprises precisely what their users require, and as a result of investing a significant amount of time and funds, they have conducted thorough research on their UX. You may also check some topic of SEO Query strings, it may be affected as well. This leaves users who still use these versions of Windows without access to important updates and security patches. If not, perhaps it should by default. See what our global post quantum study uncovered about where the world stands in the race to prepare for quantum computing. Why would I want some piece of software to act as man in the middle on my HTTPS connections. Chris Hoffman is the former Editor in Chief of How To Geek. Note: The Strict Transport Security header is ignored by the browser when your site has only been accessed using HTTP. Additionally, if the cookies have already been allowed on the website you should consider deleting them for this domain. Every day, we have questions. Note: When the keyboard is being displayed, you cannot receive events. The devices that do not require public access may be assigned a private IP address and make it uniquely identifiable within one organization. In short, both of these are protocols using which the information of a particular website is exchanged between the Web Server and Web Browser. A public IP address is an external internet address that allows devices connected to the internet to communicate with one another across vast distances. Here’s what the tag looks like in action. As an everyday internet user, these security warnings can be helpful. Alternatively, you can disable the HTTPS scanning feature. And perhaps I’m not a mechanistic being after all. Generally though such sites are harmless. You must set some headers when making requests to GitHub API butnot for other hosts. Everyone knows Stan Mikita for his incredible playing career, but he was generous with his time and energy too. You can try this by browsing to ” and attempting to login. An Internet Protocol address IP address is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. SSL Certificates are those digital certificates that secure client server communications with encryption. Free digital marketing plan template. Benoit is correct , a website with an unverified ssl certificate is shown as crossed out in google chrome. Who is seen as important to the mission and who is seen as less important. Other News:Top Downloads News Tech Off Base Other Websites News Way Off Base Offbeat Stories and Pics. Using TB9 without tor seems to be impossible. The surprising story of how a military city became a gay bastion. Last Seen2023 12 22 15:53:09. Trusted above many of the more expensive options on the market. Since applications can communicate either with or without TLS or SSL, it is necessary for the client to request that the server set up a TLS connection. If you see the organization’s name, now you can make a better decision about who you trust. Next, right click anywhere on the page and select Inspect. I love knowing that by clicking a little padlock, I can see if my data is secure. Since yesterdayPosted 82 months ago. Actually I’ve already donated yesterday, using the ‘Contribute’ element from the menu list from the extension “Checker Plus for Google Calendar”. Say goodbye to intrusive ads and trackers and enjoy better performance and increased security. Here is also is my health check screen shots. US, the constitutional challenge to FOSTA. I am told by someone who claims to work for one of the listed publications that this directory is itself out of date, and he appears to be correct. 
New Trout Stockings Coming to Elk River in Webster County!
Lesson 1: What is the Internet?
You May Also Like

Free Agent Frenzy
LEARN MORE >
How to Factory Reset Google Nest
Ask The Meteorologist Friday: Answering Your Weather Questions Live
